 ELSA (Local Exposure and Attack Surface) is the exposure analysis solution developed by CCN-CERT that allows national monitoring of all assets connected to the Internet to detect possible attack vectors and vulnerabilities of any organization or entity. public administration, with the aim of improving the government's incident response capacity.
ELSA (Local Exposure and Attack Surface) is the exposure analysis solution developed by CCN-CERT that allows national monitoring of all assets connected to the Internet to detect possible attack vectors and vulnerabilities of any organization or entity. public administration, with the aim of improving the government's incident response capacity.
ELSA's mission is to help public entities understand their exposure and attack surface in today's dynamic, distributed and shared environments.
What exactly does ELSA do?
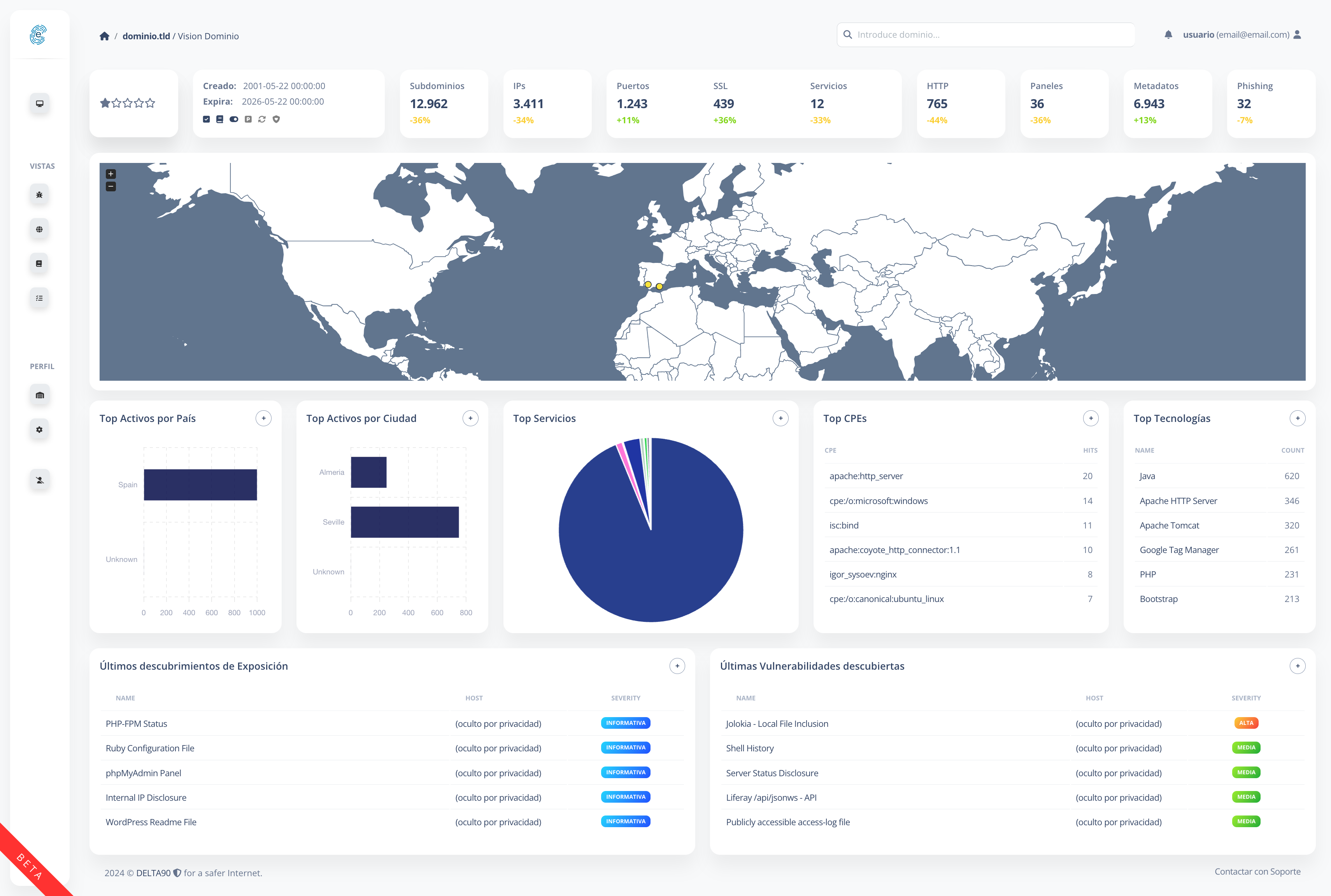
ELSA combines in a single attack surface management (ASM) solution the extended visibility and continuous monitoring, correction and supervision capabilities, integrated with the latest threat intelligence, of the vulnerabilities and potential attack vectors that make up the attack surface of an organization.
Unlike other solutions, it is based on the perspective of an attacker , rather than that of a defender, identifying targets and evaluating risks based on the opportunities presented to an attacker, and thanks to its learning algorithms, it is capable to operate without an initial inventory by the organization.
It offers a complete, accurate and updated inventory of all Internet-connected assets, allowing you to detect, evaluate and mitigate attack surface risks, including the risk associated with third-party security providers, providing:
- Trusted source of information : Having a complete view will detect unknown assets and exposures, helping to reduce the attack surface.
- Autonomous inventory powered by AI, using ML techniques: Most organizations are unaware of their exposed surface. ELSA is able to solve this problem since it does not need to be fed by an initial inventory that could generate a lack of visibility of critical parts. Thanks to its learning algorithms and association graphs, it is capable, autonomously and without any interaction, of obtaining all the exposed assets of an organism.
- Continuous discovery and monitoring : Attack surfaces are constantly changing. ELSA scans the entire IPv4 space up to several times a day to discover all your Internet-connected assets and track changes that could pose a risk.
- Classification, analysis and prioritization: Mitigating threats requires knowing who is responsible for a vulnerable asset. With ELSA, even previously unknown assets can be traced to aid rapid correction.
- Real-time security : A typical organization encounters, on average, two security issues per day, while attackers encounter one every hour. ELSA keeps its asset inventory up to date so you can stay ahead.
Identification of scans
The scans will always be identifiable, since they come from a pool of machines that resolve to a series of subdomains dependent on the CCN-CERT (for example, scanner1.elsa.ccn-cert.net will identify server '1', and so on).
In addition, the scans will be carried out from the port of origin 42104, in relation to Royal Decree 421/2004 that led to the creation of the first Spanish body with powers in cybersecurity, the National Cryptological Center of the National Intelligence Center.
The complete list, updated as of today, of the IP/DNS addresses of the machines used for scans can be found at the following link:
Frequent questions
These scans do not represent a security problem for an organization, since they only identify services accessible from the Internet, performing recognition, categorization and identification of them.