
Detección temprana de amenazas en Sistemas de Control Industrial
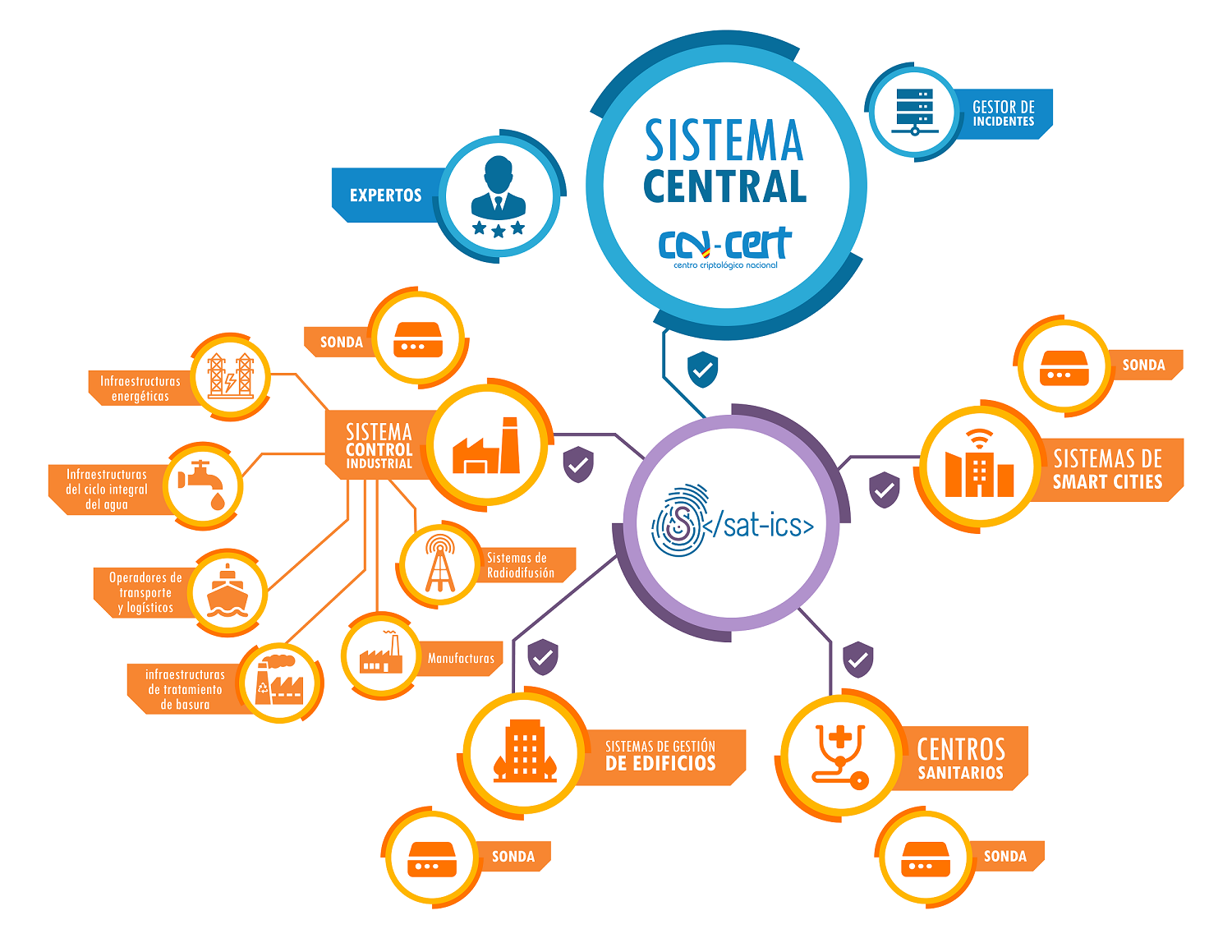
El SAT-ICS es un servicio desarrollado e implantado por el CCN-CERT para la detección en tiempo real de las amenazas e incidentes existentes en el tráfico en las redes de control y supervisión industrial del Organismo adscrito. A él puede adherirse cualquier Organismo perteneciente al Sector Público o a empresas y organizaciones de interés estratégico para el país que dependan para su operación de tecnologías ICS.
No obstante, hasta hace relativamente poco, dentro de la categoría de sistemas de control industrial solo encajaban los sistemas más tradicionales: sistemas encargados del control de las plantas industriales y sus componentes típicos: actuadores, instrumentación, PLC, remotas, software SCADA, etc. La convergencia tecnológica que estamos viviendo en los últimos años ha provocado la aparición de todo un nuevo conjunto de dispositivos y sistemas que podemos denominar ciberfísicos: se trata de todo el equipamiento con capacidad de procesamiento y conectividad que, además, permite una interacción con el mundo físico. En la actualidad, y como resultado del proceso de integración de estas nuevas tecnologías, en este grupo podemos incluir nuevos entornos. Algunos ejemplos son:
- Infraestructuras del ciclo integral del agua (captación, tratamiento (ETAP y EDAM), almacenamiento, distribución, saneamiento y depuración (EDAR))
- Operadores de transporte y logísticos (autoridades portuarias, aeroportuarias, transporte terrestre, almacenes automatizados o grandes logísticas)
- Infraestructuras energéticas (generación, transporte, distribución eléctrica, plantas de regasificación y almacenamientos de hidrocarburos)
- Infraestructuras de tratamiento de residuos
- Sistemas de radiodifusión
- Manufactura
- Centros sanitarios
- Institutos y centros de investigación
- Componentes de Smart Cities (sistemas de gestión de alumbrado público, control de tráfico, etc.)
- Sistemas de gestión de edificios (BMS)
La misión de este sistema es detectar patrones de distintos tipos de ataque y amenazas mediante el análisis del tráfico de red, incluyendo el tráfico en protocolos industriales gracias a capacidades de DPI (Deep Packet Inspection).
SAT-ICS se basa en el análisis del tráfico de red de las redes de comunicación de estos sistemas, con el objetivo de detectar en tiempo real multitud de tipos de ataques, evitando su expansión, respondiendo de forma rápida ante el incidente detectado y, de forma general, generar normas de actuación que eviten futuros incidentes.
Detección temprana de amenazas:
- Detección basada en reglas IDS. Actualización de reglas de forma diaria.
- Detección basada en comportamiento. Análisis del comportamiento habitual en la red.
- Inspección profunda de los protocolos industriales:
(*) El listado de protocolos se actualiza según necesidad. Existe la posibilidad de implementar el análisis de protocolos específicos desarrollados a medida para un Organismo.
Mapa de activos:
- Apoyo a la gestión de las redes mediante la realización pasiva de un mapa de activos y la identificación del flujo de comunicaciones entre los mismos, hacia/desde otras redes o Internet.
- Inventariado de activos implicados en la monitorización.
Informes y estadísticas de incidentes:
Los usuarios pueden acceder en tiempo real a información relevante de los eventos generados por la sonda de su organismo, a informes periódicos y a la información de los incidentes de seguridad notificados a través de un portal accesible en Internet. Cada Organismo puede ver exclusivamente los eventos e informes relacionados con su red monitorizada.
Despliegue del SAT-ICS:
Para su puesta en marcha es necesaria la instalación de una sonda individual en la red del Organismo, así como las configuraciones necesarias en la electrónica de red para enviar hacia la sonda el tráfico a analizar. La sonda es totalmente pasiva y no interfiere en ningún caso en el proceso.
- La conexión entre la sonda y el sistema central se realiza siempre de forma segura, a través del establecimiento de un túnel cifrado. Esta conexión puede realizarse a través de salida a Internet del Organismo adscrito o a través de una salida dedicada. El establecimiento de este túnel cifrado se inicia desde la sonda hacia el sistema central, no siendo necesaria ninguna infraestructura adicional por parte del organismo para el establecimiento de túneles cifrados.
- La sonda se gestiona completamente desde el CCN-CERT, no siendo necesaria la realización de tareas de administración por parte del personal del Organismo. Eventualmente se solicitaría apoyo al Organismo en el caso que fuera necesaria la realización de tareas puntuales que no pudieran realizarse de manera remota.
- De forma general, la sonda vigilará las redes que el Organismo añada a la monitorización. Con los eventos recibidos se realiza una correlación avanzada de eventos en el sistema central, permitiendo la detección de ataques hacia los distintos organismos adscritos al sistema o la presencia de código dañino en estas redes.
- La gestión, actualización y mantenimiento del sistema central está a cargo del CCN-CERT, que lleva a cabo tareas de administración, maduración de las reglas de detección e inclusión de nuevas funcionalidades y herramientas. De hecho, periódicamente se realiza la integración de numerosas reglas de detección, propias y externas, completando y ampliando la inteligencia del servicio y su capacidad de detección. Las reglas propias son generadas a partir de la información obtenida durante la investigación de otros incidentes de seguridad y a partir de la información recibida de otros organismos con los que se mantiene un intercambio de información referente a incidentes de seguridad.
Contexto
 Debido a la convergencia tecnológica que estamos viviendo en los últimos años, los equipos existentes en los centros sanitarios cuentan con nuevas capacidades de interacción. Del mismo modo, han aparecido nuevos dispositivos y sistemas que también están interconectados y que, de presentarse algún ataque o abuso en su utilización, podrían tener un impacto directo en la seguridad de los pacientes.
Debido a la convergencia tecnológica que estamos viviendo en los últimos años, los equipos existentes en los centros sanitarios cuentan con nuevas capacidades de interacción. Del mismo modo, han aparecido nuevos dispositivos y sistemas que también están interconectados y que, de presentarse algún ataque o abuso en su utilización, podrían tener un impacto directo en la seguridad de los pacientes.
El Sistema de Alerta Temprana ICS (SAT-ICS) del CCN-CERT permite la detección en tiempo real de las amenazas e incidentes acaecidos, analizando el tráfico de las redes asociadas a estos dispositivos y permitiendo la rápida respuesta ante un posible incidente de seguridad. Algo crucial si tenemos en cuenta que en estos entornos cada minuto es primordial para frenar el impacto.
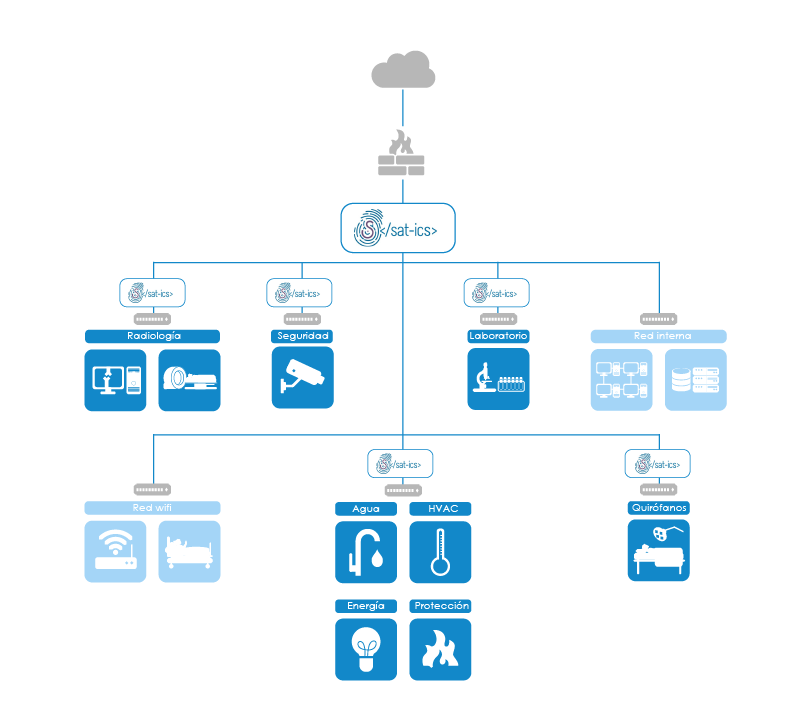
Figura 1. Monitorización de entornos médicos
¿Qué aporta el SAT ICS a los sistemas sanitarios?
- Detección de ataques e incidentes
- Inventario y mapa de activos
- Detección en base a anomalías
- Correlación
- Elaboración de casos de uso específicos
- Informes estadísticos y soporte a la resolución de incidentes
Contexto
 Los entornos portuarios se han convertido en infraestructuras clave debido al auge del comercio internacional y la globalización. La búsqueda de una mayor eficiencia en las operaciones y la competencia entre puertos ha llevado a una digitalización del sector masiva en los últimos años que no es ajena a las infraestructuras industriales que permiten su operación. Pero este proceso ha abierto también una puerta a riesgos que debemos de ser capaces de identificar y gestionar, ya que de materializarse pueden resultar en un impacto grave en las operaciones portuarias.
Los entornos portuarios se han convertido en infraestructuras clave debido al auge del comercio internacional y la globalización. La búsqueda de una mayor eficiencia en las operaciones y la competencia entre puertos ha llevado a una digitalización del sector masiva en los últimos años que no es ajena a las infraestructuras industriales que permiten su operación. Pero este proceso ha abierto también una puerta a riesgos que debemos de ser capaces de identificar y gestionar, ya que de materializarse pueden resultar en un impacto grave en las operaciones portuarias.
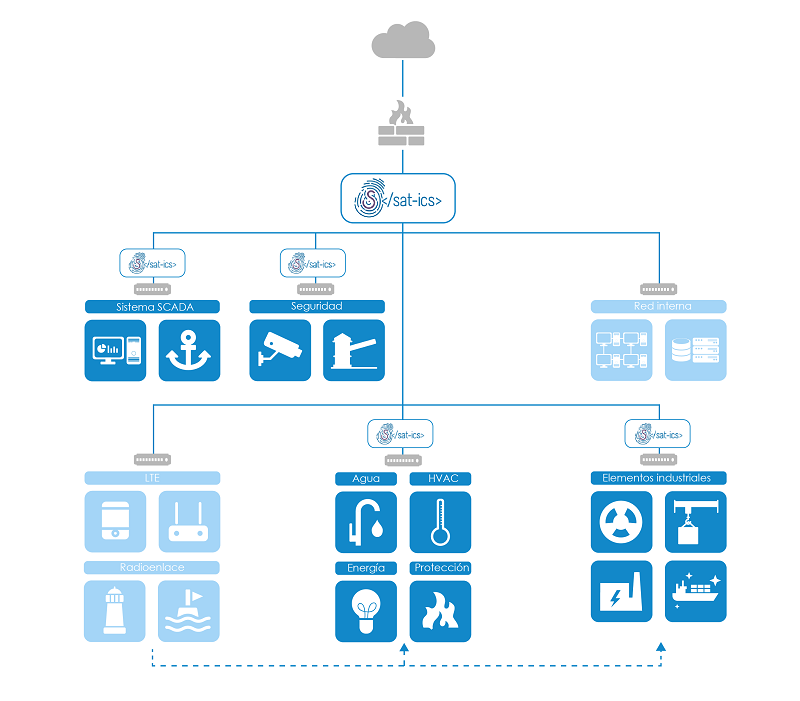
Figura 1. Monitorización de entornos portuarios
¿Qué aporta el SAT ICS a los sistemas de los entornos portuarios?
- Detección de ataques e incidentes
- Inventario y mapa de activos
- Detección en base a anomalías
- Correlación
- Elaboración de casos de uso específicos
- Informes estadísticos y soporte a la resolución de incidentes
Contexto
 Los procesos relacionados con el sector del agua son considerados servicios esenciales y es por ello que deben proveerse los recursos necesarios para su protección. Dado el creciente número de ciberataques a infraestructuras críticas no debe descuidarse el impacto potencial de uno de estos incidentes sobre poblaciones completas.
Los procesos relacionados con el sector del agua son considerados servicios esenciales y es por ello que deben proveerse los recursos necesarios para su protección. Dado el creciente número de ciberataques a infraestructuras críticas no debe descuidarse el impacto potencial de uno de estos incidentes sobre poblaciones completas.
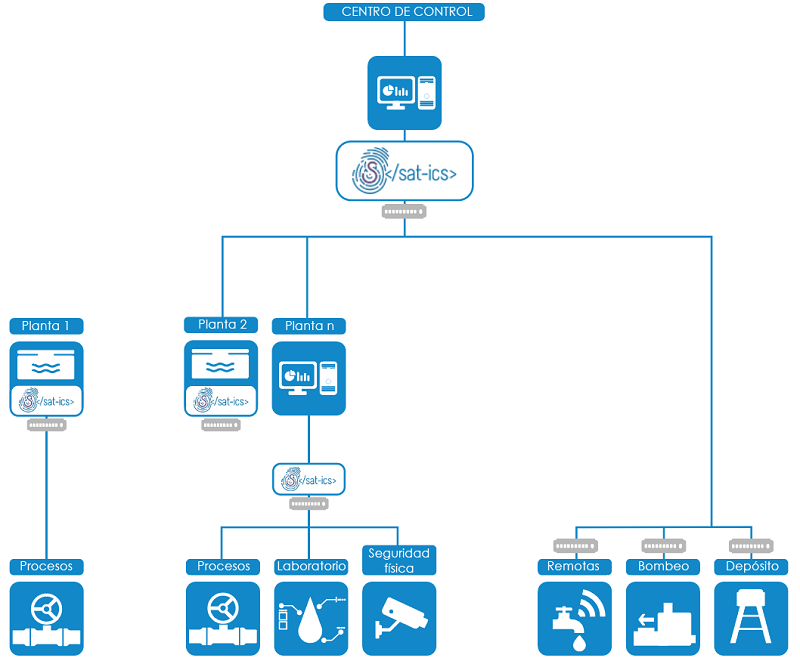
Figura 1. Monitorización de infraestructuras del ciclo integral del agua
¿Qué aporta el SAT ICS a las infraestructuras del ciclo integral del agua?
- Detección de ataques e incidentes
- Inventario y mapa de activos
- Detección en base a anomalías
- Correlación
- Elaboración de casos de uso específicos
- Informes estadísticos y soporte a la resolución de incidentes
Contexto
 El término Smart City o ciudad inteligente es usado para referirse a ciudades basadas en un desarrollo sostenible, que usan las diferentes tecnologías de la información y comunicación para la gestión y prestación de sus diferentes servicios. En el contexto de una ciudad inteligente, los sistemas de control industrial y demás sistemas IIoT, juegan un papel esencial para asegurar el funcionamiento eficiente y seguro de las diversas infraestructuras y servicios que la hacen posible. Estos sistemas integran y automatizan una amplia gama de procesos para mejorar la calidad de vida de los ciudadanos, permiten la optimización de los recursos y ayudan a reducir el impacto ambiental, entre otras funcionalidades. Sin embargo, la introducción de estos sistemas ha abierto también una puerta a riesgos que debemos ser capaces de identificar y gestionar, evitando cualquier posible impacto grave en la seguridad de los ciudadanos.
El término Smart City o ciudad inteligente es usado para referirse a ciudades basadas en un desarrollo sostenible, que usan las diferentes tecnologías de la información y comunicación para la gestión y prestación de sus diferentes servicios. En el contexto de una ciudad inteligente, los sistemas de control industrial y demás sistemas IIoT, juegan un papel esencial para asegurar el funcionamiento eficiente y seguro de las diversas infraestructuras y servicios que la hacen posible. Estos sistemas integran y automatizan una amplia gama de procesos para mejorar la calidad de vida de los ciudadanos, permiten la optimización de los recursos y ayudan a reducir el impacto ambiental, entre otras funcionalidades. Sin embargo, la introducción de estos sistemas ha abierto también una puerta a riesgos que debemos ser capaces de identificar y gestionar, evitando cualquier posible impacto grave en la seguridad de los ciudadanos.
Dispositivos implicados
Existe una gran diversidad de dispositivos que pueden interactuar en el entorno de una ciudad inteligente. Es posible encontrar tanto dispositivos OT tradicionales (sensores y controladores) como otros dispositivos IoT o IIoT. Existen multitud de tipologías de despliegue de dispositivos, generalmente, este parque diverso de dispositivos se conecta y gestiona de diferentes formas como; puertas de enlace inalámbricas, pasarelas serie, 4G/5G, fibra, ethernet, etc. Estos elementos actuarían como elementos para, por ejemplo, el filtrado de datos, gestión de dispositivos, control de acceso y comunicación compartida con redes y aplicaciones.
Estos dispositivos se pueden desplegar tanto con acceso a la propia red del Ayuntamiento, como pertenecer a terceros y que la comunicación pueda realizarse directamente o mediante concentradores, de forma inalámbrica o cableada. La comunicación de estos dispositivos también puede extenderse hacia la nube. Este entorno cloud se encarga de consolidar y analizar datos, procesar eventos, proporcionar acceso a los datos a las distintas aplicaciones y llevar a cabo diversas funciones adicionales. No existe una única arquitectura que represente todos los tipos de infraestructuras desplegadas y modos de explotación posibles dentro del sector, por lo que los puntos de red monitorizados dependen de la realidad de cada caso. Aunque esta variedad de tipologías de despliegue dificulta la monitorización, es posible analizar el tráfico en los puntos en los que estos sistemas se interconectan hacia los sistemas centrales y bases de datos. Estas comunicaciones requieren de una supervisión y control para evitar cualquier posible abuso.
¿Por qué SAT-ICS?
El sistema alerta temprana ICS (SAT-ICS), permite la detección a tiempo real de las amenazas e incidentes en el tráfico de las redes asociadas a estos dispositivos, e incluso una rápida reacción ante un posible incidente de seguridad.
Monitorización de ciudades inteligentes centralizadas
Como se puede observar en la arquitectura, tenemos 3 zonas diferenciadas, y dos opciones de monitorización. En el caso de que se pueda acceder al cloud gateway, porque esté en red local, se podrá monitorizar (Mon 1), en caso contrario tendremos solo un punto de monitorización en nuestra red local (Mon 2).
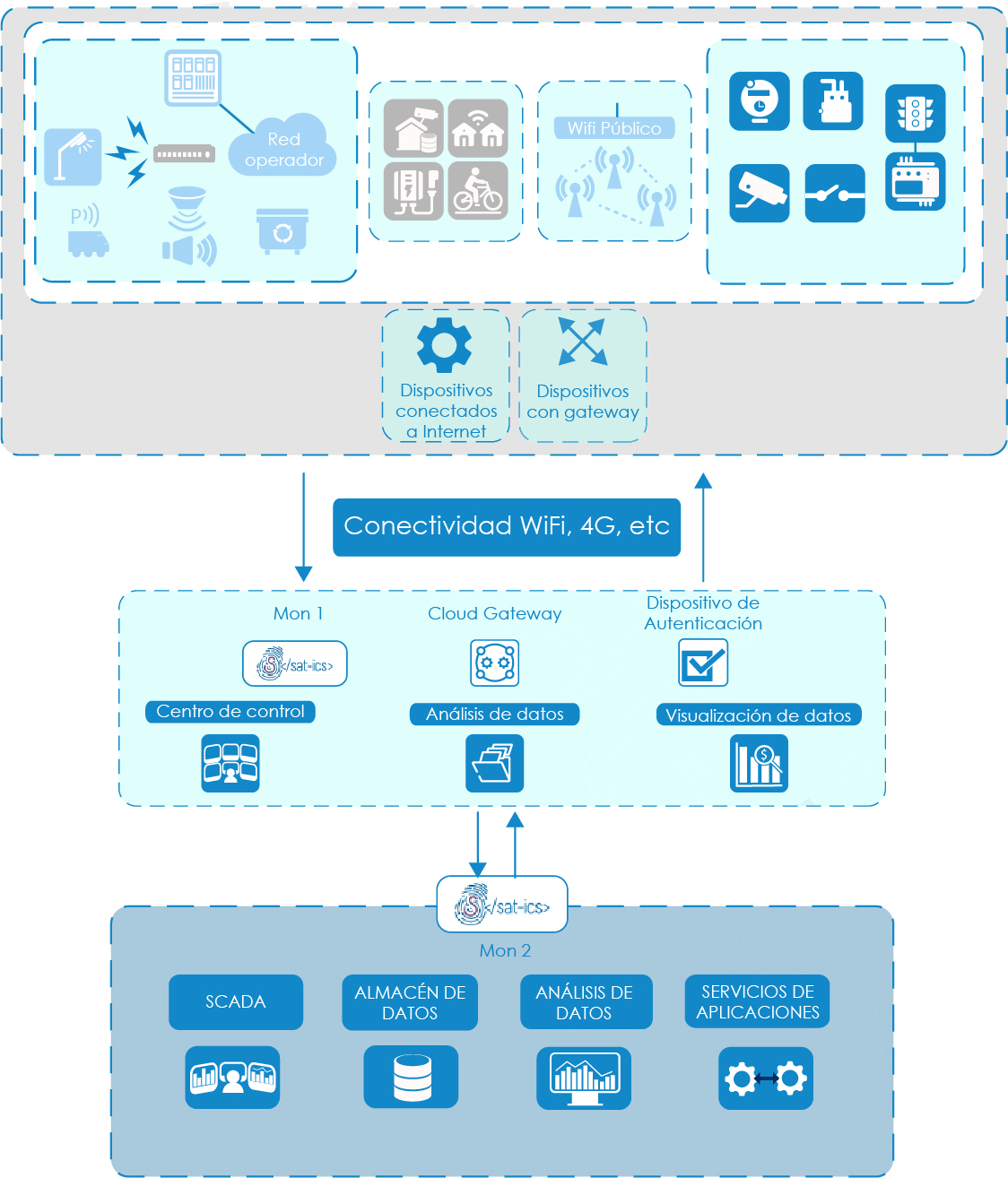
Figura 1. Monitorización en Smart Cities
¿Qué aporta el SAT ICS a las infraestructuras en Smart Cities?
- Detección de ataques e incidentes
- Inventario y mapa de activos
- Detección en base a anomalías
- Correlación
- Elaboración de casos de uso específicos
- Informes estadísticos y soporte a la resolución de incidentes
FAQ
Un sistema ciberfísico es todo aquel dispositivo que integra capacidades de computación, almacenamiento y comunicación para controlar e interactuar con un proceso físico. Los sistemas ciberfísicos están, normalmente, conectados entre sí y también con servicios remotos de almacenamiento y gestión de datos.
La sonda SAT ICS puede desplegarse en diferentes entornos, tales como:
- Infraestructuras del ciclo integral del agua (captación, tratamiento (ETAP y EDAM), almacenamiento, distribución, saneamiento y depuración (EDAR)).
- Operadores de transporte y logísticos (autoridades portuarias, aeroportuarias, transporte terrestre, almacenes automatizados o grandes logísticas).
- Infraestructuras energéticas (generación, transporte, distribución eléctrica, plantas de regasificación y almacenamientos de hidrocarburos).
- Infraestructuras de tratamiento de residuos.
- Sistemas de radiodifusión.
- Manufactura.
- Centros sanitarios.
- Institutos y centros de investigación.
- Componentes de Smart Cities (sistemas de gestión de alumbrado público, control de tráfico, etc.).
- Sistemas de gestión de edificios (BMS - Building Management Systems).
La sonda es un servidor de alto rendimiento que permite el análisis del tráfico de la red del Organismo adscrito, la generación de eventos específicos de seguridad y su envío de forma segura al sistema central. Consta de los siguientes elementos:
- La interfaz de gestión, que se conecta a la red del Organismo para enviar al sistema central del SAT los eventos generados por la sonda.
- Los interfaces de análisis, que reciben el tráfico a analizar y que no tienen dirección IP, siendo totalmente transparentes a la red.
- Un sistema de detección de intrusiones de red (NIDS), con reglas de detección específicas de diferentes fuentes (incluyendo específicas para sistemas SCADA) y de creación propia.
- Un conjunto de agentes específicos para detectar anomalías en entornos ICS, incluyendo un análisis de la estructura de comunicaciones de la red y los disectores de protocolos industriales.
- Un recolector de los eventos detectados para su envío al Sistema Central. Este agente inicialmente estará configurado para el análisis de los eventos generados por las distintas herramientas de detección que se incorporen.
La sonda puede implantarse en distintos puntos de la red dentro de la infraestructura del Organismo, típicamente en los anillos de comunicaciones industriales o en las interconexiones entre los niveles de control, campo y supervisión y sus comunicaciones con el exterior.
Dependiendo de la arquitectura de la red y las capacidades que esta ofrezca para la monitorización, se estudiará junto con el Organismo la estrategia que mejor se adapte a sus posibilidades, que se pueden clasificar a grandes rasgos en 2 tipos:
-
Monitorización interna de las redes:
En aquellos casos en los que sea posible realizar un “puerto espejo” de la electrónica de red interna de las distintas redes de control o supervisión, se podrá monitorizar el tráfico interno de dichas redes de manera diferenciada, así como el tráfico que entre o salga de estas.
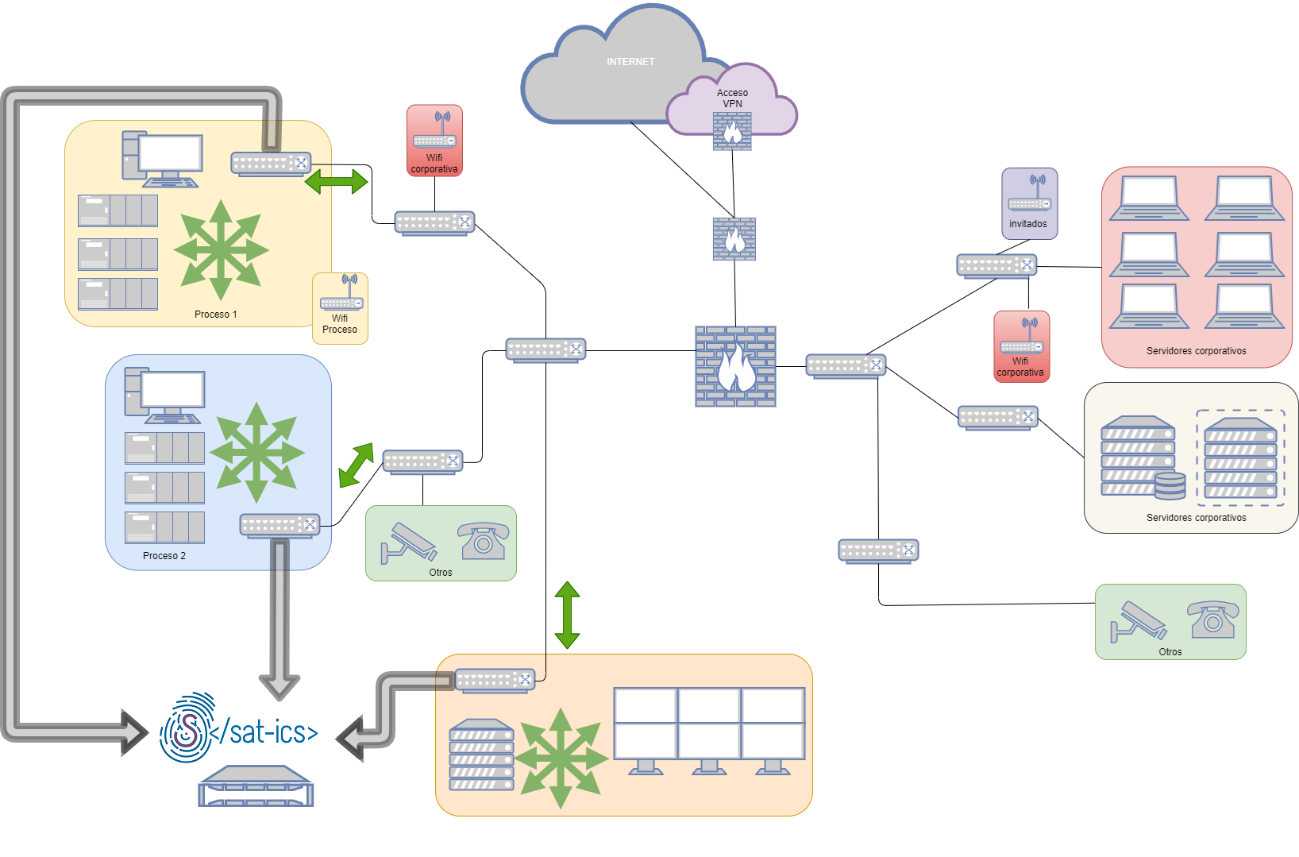
Esquema de monitorización interna -
Monitorización perimetral interna:
En aquellos casos en los que no se considere adecuado realizar un “puerto espejo” de la electrónica de red interna de las distintas redes de control o supervisión, se podrá (si la tecnología de la infraestructura lo permite) realizar una monitorización del tráfico que llega al cortafuegos o router que segmenta las distintas redes, con el fin de monitorizar todo el tráfico que entre o salga de las redes de sistemas ciberfísicos.
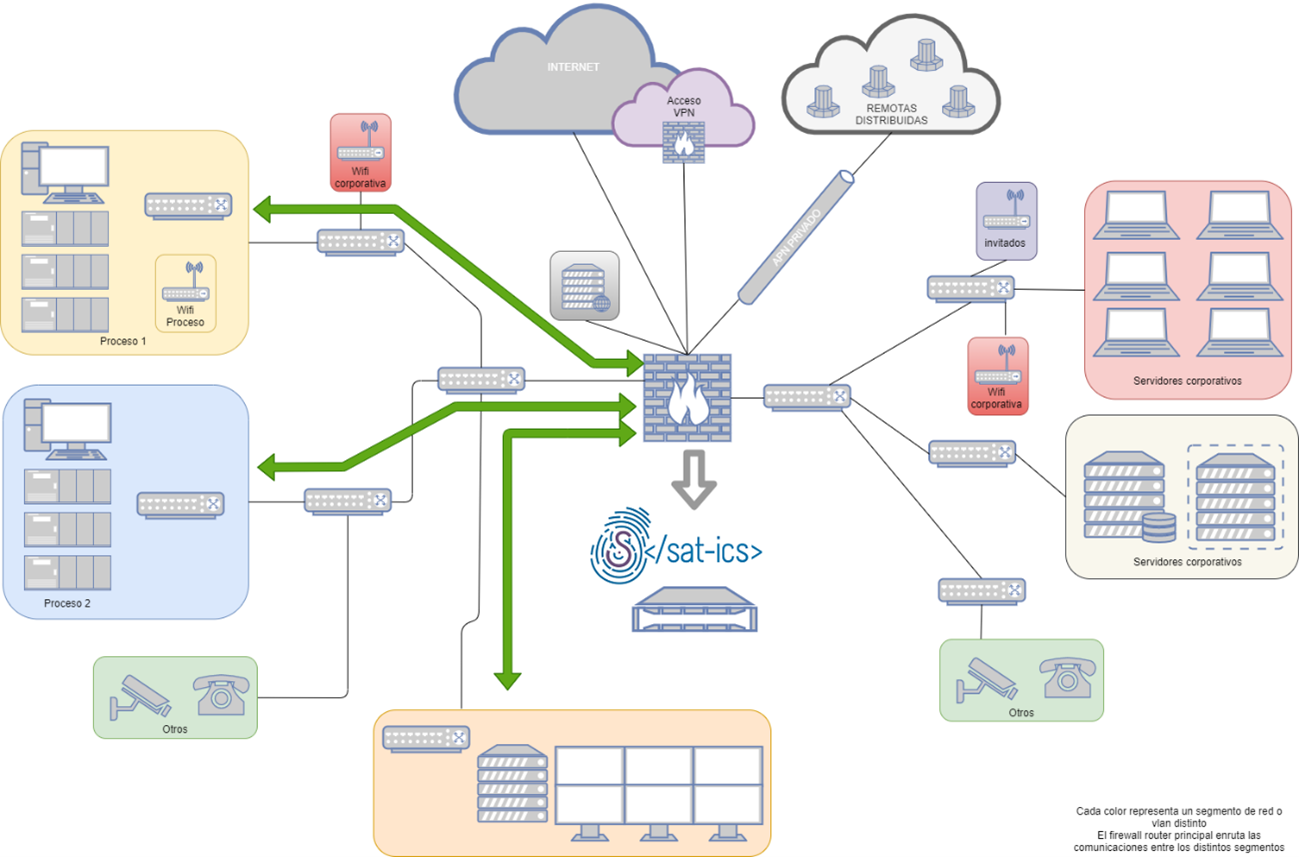
Esquema de monitorización perimetral
El sistema central es el encargado de la recolección de la información proveniente de las distintas sondas y de la correlación de eventos para detectar incidentes de seguridad.
Está compuesto por diferentes elementos:
- Recolector de eventos. Es el encargado de recibir los eventos que provienen de los diferentes sistemas a analizar y de enviarlos al bus de eventos del que se nutre el siguiente elemento.
- Motor de correlación. Es el encargado de procesar la información que llega al bus de eventos. Este elemento del sistema implementa reglas de correlación que son las que deciden si se genera o no una alerta en respuesta a los eventos recibidos.
- Consola única de operador. Es la que permite el análisis de las alertas generadas tras la correlación de los eventos recibidos por el sistema.
- Cuadro de mando activo. Es el que presenta información relativa a los procesos monitorizados y permite la visualización de indicadores.
La gestión, actualización y mantenimiento del sistema central está a cargo del CCN-CERT, que con un equipo de expertos en ciberseguridad lleva a cabo tareas de administración, maduración de las reglas de detección e inclusión de posibles nuevas fuentes.
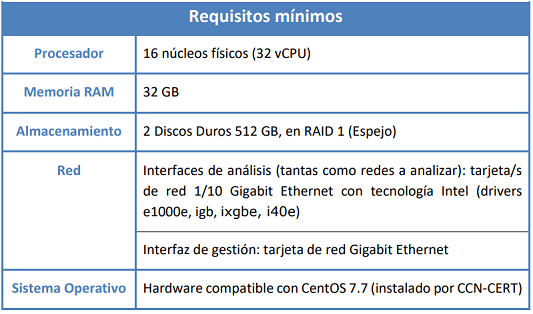
Dependiendo de las características de la red y de los sistemas monitorizados, se recomiendan dos tipos diferentes de sonda, cuyos requerimientos hardware para el adecuado funcionamiento son los siguientes:
1) Sonda Estándar:
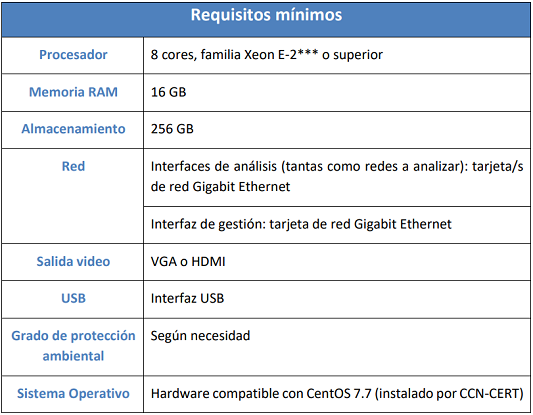
2) Minisonda:
La minisonda (**) SAT-ICS está pensada para instalaciones industriales donde no es posible instalar la sonda SAT-ICS estándar por uno o varios de los siguientes motivos:
- Se dispone de poco espacio físico para la instalación de la sonda.
- Necesidades especiales de montaje en rack (carril DIN, etc.).
- Condiciones ambientales desfavorables (humedad, temperatura, polvo, etc.).
- El tráfico a analizar no supera 1Gbps de throughput.
(*) Los requerimientos hardware pueden sufrir variaciones en un futuro debido a la incorporación de nuevas capacidades de detección que incurran en una mayor demanda computacional.
(**) Cabe destacar que son equipos que van a estar trabajando 24x7 los 365 días del año. Es requerimiento esencial el uso de un equipo de tipo servidor, tanto si es enracable como para bandeja o para carril DIN. Debe evitarse el uso de equipos convencionales de puesto de trabajo.
El transporte de los eventos se realiza de forma segura a través de un túnel cifrado por la salida de Internet del Organismo hacia el Sistema Central, con lo que la confidencialidad e integridad de la información queda garantizada. La conexión entre la sonda individual y el sistema central se puede establecer de dos formas:
- Conexión de la sonda a Internet a través de la infraestructura de Internet del Organismo adscrito.
- Conexión directa de la sonda a una conexión a Internet independiente de la red del Organismo.
Las sondas únicamente envían hacia el sistema central alertas de seguridad generadas tras la detección de algún tipo de evento, definidos en las reglas de detección integradas en el sistema, y que responden a patrones de tráfico potencialmente dañinos, de comportamientos conocidos de determinado tipo de código dañino o a usos no habituales o potencialmente peligrosos de los sistemas de control industrial. En ningún momento se realiza un envío del tráfico de red del Organismo hacia el sistema central, manteniéndose así la privacidad en las comunicaciones.
La finalidad de la sonda es detectar ataques que se produzcan en las redes del Organismo y dar una respuesta rápida y eficaz ante incidentes, aunque el trabajo de detección se centrará principalmente en detectar actividad anómala o potencialmente peligrosa en estos sistemas y en la detección de intentos de intrusión sobre estas redes. La base del servicio radica en la identificación de aquellas situaciones que pueden suponer un riesgo para la infraestructura y en la definición de reglas para su detección, partiendo del conocimiento de la forma en que se explotan este tipo de sistemas.
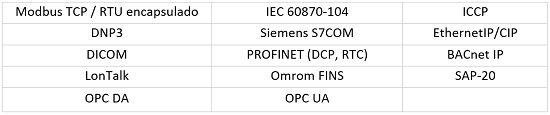
Una característica del sistema SAT-ICS es que permite trabajar con los protocolos industriales, analizando también el payload de los paquetes (Deep Packet Inspection o DPI) para identificar el fin de un determinado comando: descargar o cargar programas en los PLC, escanear la red para identificar los equipos que forman parte de ella o el envío de comandos potencialmente peligrosos, por ejemplo. Actualmente es posible analizar el tráfico de los protocolos recogidos en la siguiente tabla:
Nuevos protocolos se añaden a la lista continuamente. También existe la posibilidad de implementar el análisis de protocolos específicos desarrollados a medida para un Organismo.
El portal del SAT es el lugar en el que el personal responsable de la ciberseguridad del Organismo adscrito puede visualizar en tiempo real los eventos generados por su sonda y que han sido enviados al sistema central. Además, permite acceder a la herramienta LUCIA para la gestión de los incidentes que hayan sido detectados por la sonda y comunicados al organismo.
Del mismo modo, también es posible el acceso a estadísticas e informes sobre el servicio ofrecido por este Sistema de Alerta Temprana.
A través de este portal también es posible visualizar de forma gráfica el mapa de activos de las redes monitorizadas, con sus correspondientes comunicaciones habituales o anómalas y enriquecidas con información adicional extraída de forma pasiva. Este mapa de activos proporciona capacidades de búsqueda y filtrado para facilitar la investigación de incidentes o simplemente aumentar el conocimiento de la red.

Mapa de activos y conexiones
Adicionalmente, en el portal SAT se ofrece a los Organismos un cuestionario que permite a los operadores del sistema adaptar el tipo de alertas que se generan a sus características específicas y capacidad de gestión de incidentes de seguridad.

Portal Sistema de Alerta Temprana
La gestión y administración de la sonda se realiza por el personal técnico del CCN-CERT, para mantener un sistema lo más homogéneo posible. Entre las tareas de gestión y administración se incluyen la actualización diaria de las reglas de detección, actualizaciones de sistema operativo, actualización de las aplicaciones, aplicación de parches de seguridad de sistema operativo y de aplicaciones, particularización de las reglas de detección, etc.
Únicamente tendrán acceso a la información del Organismo adscrito los responsables de la seguridad TIC seleccionados por el propio Organismo para tal efecto y los administradores del sistema, es decir, el equipo de expertos del CCN-CERT que monitoriza el sistema central de sondas. Ninguna otra persona tendrá acceso a esta información. Es importante saber que ningún Organismo tendrá acceso a la información de otros organismos adscritos y únicamente podrá ver el estado de seguridad de su propia red, si bien sí que será usada la detección de eventos distribuida para la generación de la inteligencia del sistema de forma automatizada. En este sentido, como en todas las materias competencia del Centro Criptológico Nacional, la política a seguir será la de mantener en todo momento la confidencialidad de la información tratada.
Cualquier Organismo perteneciente al Sector Público o a empresas y organizaciones de interés estratégico para el país que dependan para su operación de sistemas ciberfísicos de todo tipo puede adherirse al Sistema de Alerta Temprana SAT-ICS, contactando con el CCN-CERT a través de la cuenta de correo 
Para la recepción de los incidentes el Organismo que esté adscrito al Sistema de Alerta Temprana SAT-ICS deberá disponer de una cuenta de correo a la que enviar la notificación de los incidentes de seguridad. Esta cuenta de correo deberá ser única, por lo que se recomienda al Organismo la creación de una lista de distribución que reciba todo el personal que vaya a encargarse de la investigación de los incidentes de seguridad.
La información referente a los incidentes de seguridad detectados por el personal técnico del CCN-CERT estará disponible en la herramienta LUCIA, al que tendrán acceso los responsables de seguridad de los Organismos adheridos a este servicio, donde podrán realizar el seguimiento de los incidentes notificados y donde podrán informar de las acciones llevadas a cabo para la resolución del mismo.
LUCIA es la herramienta de ticketing para la gestión de incidentes de seguridad desarrollada por el CCN-CERT (puede encontrar más información referente a LUCIA en https://www.ccn-cert.cni.es/herramientas-de-ciberseguridad/lucia.html).
Aunque la información relativa a los incidentes de seguridad notificados al Organismo se encontrará en la herramienta LUCIA, ante la posible necesidad de intercambio de información referente a los incidentes de seguridad a través del correo electrónico, será necesario que el organismo genere un par de claves PGP/GPG para intercambiar información de manera cifrada en el caso que fuese necesario. Una vez generadas las claves PGP/GPG asociadas a esta cuenta de correo, el Organismo deberá remitir al CCN-CERT la clave pública para poder cifrar la información que éste quisiera remitir de manera cifrada. Igualmente, el CCN-CERT proporcionará la clave pública de la cuenta de correo utilizada para la notificación de incidentes para que el Organismo pueda también enviarle información cifrada en caso necesario.

Más información:
- SAT-ICS
- SAT-ICS Centros sanitarios
- SAT-ICS Entornos portuarios
- SAT-ICS Infraestructuras del ciclo integral del agua
- SAT-ICS Smart Cities
Contacto:





