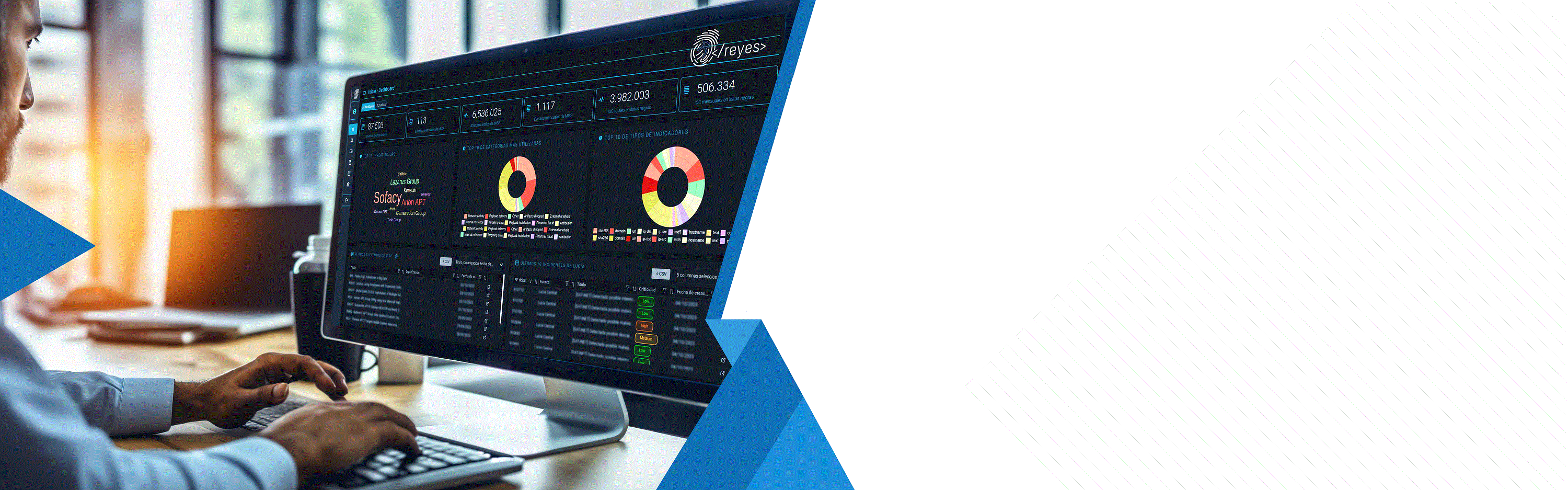
Links of interest
Cybersecurity Solutions
CCN-STIC Courses
Upcoming courses:
XXII Curso de Seguridad de las Tecnologías de la Información y las Comunicaciones (STIC)
- Del 15 al 26 de enero (Fase asíncrona: 50 h.)
- Del 29 de enero al 2 de febrero (Fase presencial: 25 h.)
- Del 5 al 9 de febrero (Fase síncrona: 25 h.)
V Curso STIC Desarrollo Seguro
- Del 15 al 19 de enero (Fase asíncrona: 25 h.)
- Del 22 al 26 de enero (Fase síncrona: 25 h.)
Latest news
El Centro Criptológico Nacional ha gestionado más de 30.000 ciberincidentes de peligrosidad muy alta y crítica en sus 20 años de trayectoria
Desde el año 2006, el Centro Criptológico Nacional ha gestionado más de 30.000 incidentes con un nivel peligrosidad muy alto o crítico.
En la última década, el número de incidentes gestionados anua...
Actualizada la guía CCN-STIC-813 sobre ciberseguridad de espacios de datos
Ya está disponible en el portal del CCN-CERT la actualización de la guía sobre los aspectos de seguridad a considerar para implantar y operar un espacio de datos.
Fecha de publicación: 22/04/2024...
Warnings / Alerts
CCN-CERT AV 07/24 Actualizaciones de seguridad para productos Cisco
Fecha de publicación: 26/04/2024
Nivel de peligrosidad: CRÍTICO
El CCN-CERT, del Centro Criptológico Nacional, informa de la publicación de dos avisos de seguridad por parte del fabricante Cisco, en...
CCN-CERT AV 06/24 Actualizaciones de seguridad para XZ Utils
Fecha de publicación: 01/04/2024
Nivel de peligrosidad: CRÍTICO
El CCN-CERT, del Centro Criptológico Nacional, informa de la publicación de un aviso de seguridad por parte del fabricante Red Hat, co...